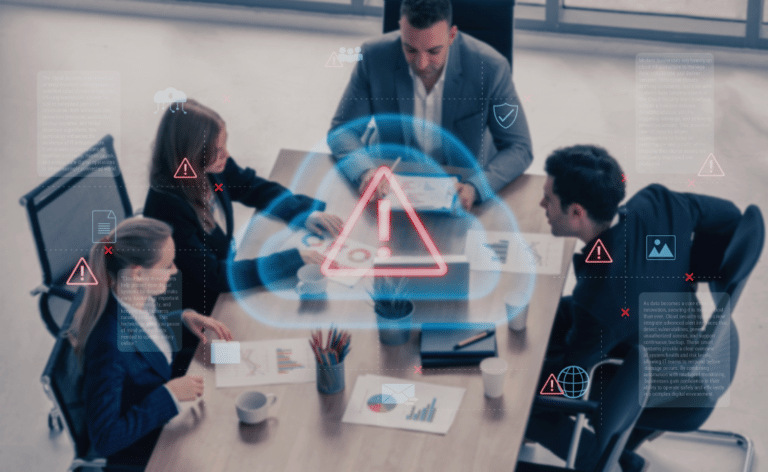
Your strategic Security Consulting
For companies that want to future-proof their security architecture and minimise cyber risks in a targeted manner, we offer in-depth security analyses, zero trust architecture consulting and compliance-oriented strategies – for resilient infrastructures, superior cloud security and legally compliant IT governance through professional security consulting.
Cybersecurity needs strategy. And advice that exposes critical vulnerabilities.
When IT security becomes a risk factor, it is rarely due to a lack of technology – but rather to distributed system landscapes, evolved structures and a lack of strategic control. Many companies only secure selectively and lose sight of the big picture: Which assets are really worth protecting? Which risks are real? And how can compliance be implemented in a technically sustainable way?
Unclear responsibilities, high audit costs and inconsistent measures lead to security gaps – ideal points of attack for cyberattacks with massive consequences for operations, data and reputation. CONVOTIS Security Consulting closes this gap with in-depth analyses, strategic architecture consulting and regulatory clarity.
Expertise that protects – for more resilient systems and fewer attack surfaces.
- Security Assessments in accordance with ISO/IEC 27001, BSI IT-Grundschutz
- Zero Trust Readiness Checks and architecture consulting
- Vulnerability management and penetration testing for web applications, APIs and networks
- Cloud security audits for Microsoft 365, Azure, AWS and sovereign cloud architectures
- Security architecture reviews for hybrid IT landscapes
- Governance, risk, and compliance workshops (including NIS2, FAIS, DORA, TISAX, GDPR)
- Tool expertise: Nessus, Burp Suite, OpenVAS, Microsoft Defender, Microsoft Sentinel
- Methodical integration into existing IT processes (e.g. ITIL, TOGAF, CIS Controls)
- Identity & Access Management Strategieberatung (IAM)



























What are the specific benefits?
More security, targeted prevention, fewer cyber risks.
How we support you.
We offer strategic Security Consulting for companies that want to reorganise their IT security holistically – from risk analysis and zero trust to compliance protection in accordance with NIS2, FAIS, DORA and ISO 27001.
Our consulting approaches are individually tailored to your IT landscape and business objectives and combine technical know-how with regulatory expertise. Whether cloud security assessment, architecture consulting or governance model – we create clarity, reduce attack surfaces and make your security strategy implementable and auditable.
As part of our Security Consulting, we start with a structured security analysis of your IT infrastructure - from on-prem systems to the cloud. We identify vulnerabilities in network architectures, operating systems, APIs and authorisation concepts. The risk assessment is based on current threat scenarios, business criticality and common standards such as ISO 27001, CVSS and BSI IT-Grundschutz. The result: a prioritised, comprehensible risk score that enables well-founded decisions and a robust security strategy.
In Security Consulting, we develop Zero Trust architectures that are based on the principle of least privilege and authenticate and authorise every request independently - regardless of network location, device or user role. We evaluate your existing access infrastructure, check identity sources, role-based authorisations, endpoint trust and cloud access models. The goal is a dynamic security architecture with granular segmentation, end-to-end multi-factor authentication (MFA) and continuous validation of sensitive resources. In this way, we create the basis for modern, resilient IT security in hybrid environments.
We develop sustainable governance structures - customised to the size of the company, risk profile and regulatory requirements. As part of our Security Consulting, we analyse existing security guidelines, define role models, implement control processes and support you in the introduction of a consistent policy framework. This includes access guidelines, acceptable use policies, incident handling and awareness concepts. The result is a documented, effective governance model that reliably combines technology, organisation and responsibility.
In Security Consulting, we develop sustainable governance structures - tailored to the size of the company, risk profile and regulatory requirements. We analyse existing security guidelines, define role models, implement control processes and support you in the introduction of a consistent policy framework. This includes access guidelines, acceptable use policies, incident handling and training concepts to increase awareness. The result is a documented, effective governance model that combines technology, organisation and responsibility.
We support your organisation in targeted preparation for internal or external audits - from ISO 27001 and TISAX to regulatory audits in accordance with DORA, NIS2 or FAIS. As part of our Security Consulting, we structure the relevant evidence, strengthen your organisation's documentation capabilities and deliver comprehensible reports for the CISO, CIO and management. With risk overviews, gap analyses and roadmaps, we make your IT security manageable and verifiable - also vis-à-vis investors, partners or supervisory authorities.
Security Consulting does not end with analysis - it translates findings into concrete action. We develop realistic roadmaps for implementing your IT security strategy, prioritise measures according to risk, effort and business impact and align them with your resources and objectives. The measures range from rights management and network protection to the introduction of secure cloud controls. We help you to implement technical and organisational measures in a structured manner - verifiably, economically and in compliance with regulations.
Your IT Transformation starts here.
Let's talk about your goals.
Whether you want to fend off targeted attacks, reorganise your IT security or implement regulatory requirements such as NIS2 and DORA – we support you with strategic Security Consulting, clear risk assessment and individual architecture consulting. Together, we will create a security structure that is auditable and future-proof.
Dive deeper into the topic.
Explore further resources.
Understanding Zero Trust. Rethinking security.
From access control to architecture strategy – this article provides a compact overview of how Zero Trust Security effectively protects modern IT infrastructures.
How secure interfaces protect your architecture
How companies protect their API landscape against attacks – for reliable interfaces and maximum data security.
FAQ
Do you have questions about the right security strategy?
In our FAQ you will find concise answers to key topics relating to IT security, compliance, risk analysis and Zero Trust.
Still have questions?
Security Consulting is strategic IT security consulting for companies - focussing on risk assessment, security architecture, compliance and governance. It is relevant when IT risks, audit pressure or growing attack surfaces need to be addressed in a structured manner - for example when introducing Zero Trust, regulatory requirements such as NIS2, FAIS or cloud transformations.
Security Consulting includes security analyses, risk and vulnerability assessments, zero trust architecture consulting, cloud security assessments, compliance strategies (e.g. NIS2, FAIS, DORA, ISO 27001), governance models and action planning. The goal is an implementable IT security strategy that securely combines technology, organisation and regulation - tailored to your corporate structure.
Security Consulting creates the basis for regulatory resilient IT security - technically and organisationally. We review your current security situation, evaluate existing controls and develop a roadmap for implementing NIS2, FAIS, DORA, ISO 27001 or TISAX. This includes governance structures, guidelines, evidence and specific measures for auditability.
A project starts with a structured security analysis. This is followed by a risk assessment, architecture workshops, compliance checks and a prioritised roadmap of measures. Depending on the objective, we also provide support with audit preparation, policy development or technical implementation.
The costs depend on the scope of the project, system complexity and compliance requirements. Entry-level packages such as a Security Quick Check or NIS2/FAIS assessment are already clearly calculable. For larger projects such as complete security strategies, we create a customised, targeted offer - tailored to your resources and priorities.